
DST40 transponder: principle of operation, history of emergence and hacking, as well as a bit of brute force practice / Sudo Null IT News

DST40 transponder: principle of operation, history of emergence and hacking, as well as a bit of brute force practice / Sudo Null IT News

DST40 transponder: principle of operation, history of emergence and hacking, as well as a bit of brute force practice / Sudo Null IT News
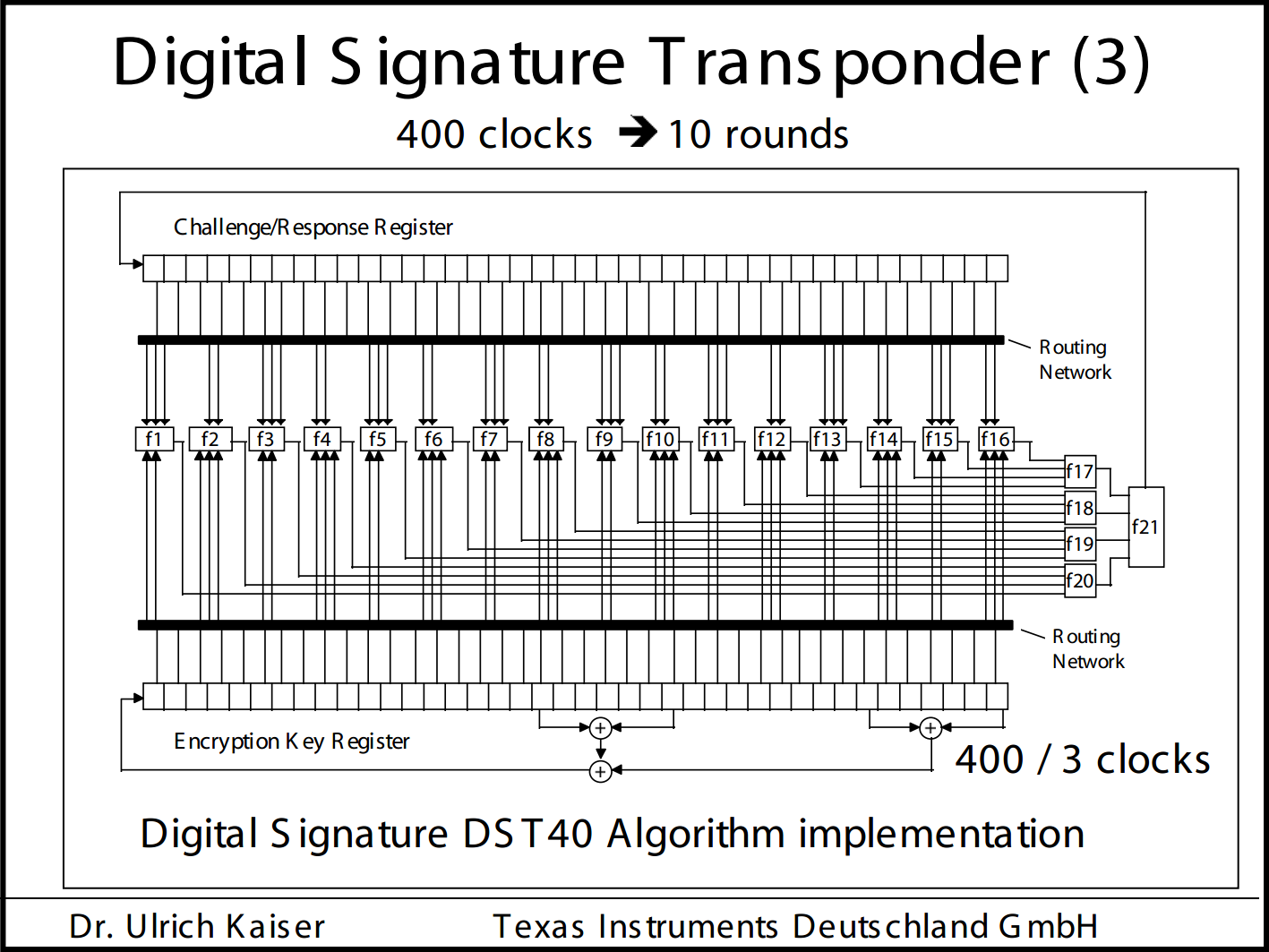
DST40 transponder: principle of operation, history of emergence and hacking, as well as a bit of brute force practice / Sudo Null IT News








