Inspiration showing sign Router Exploits. Concept meaning takes advantage of a security flaw in an application Three Colleagues Carrying S Decorating Stock Photo - Alamy

Exploit revealed for remote root access vulnerability affecting many router models - Help Net Security






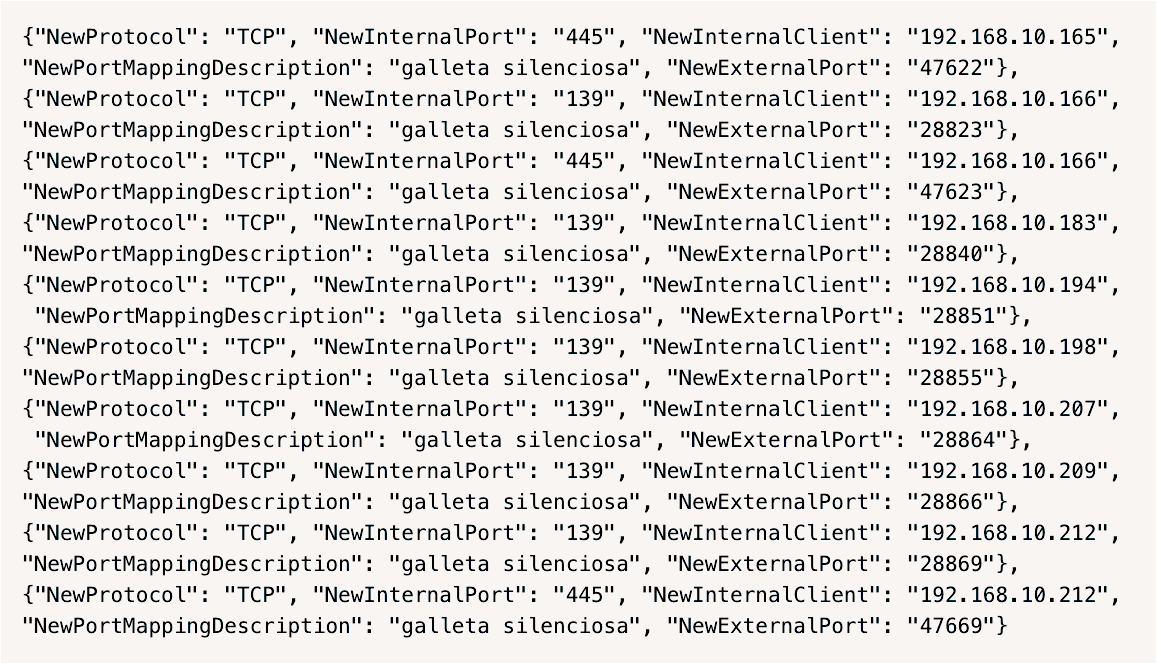



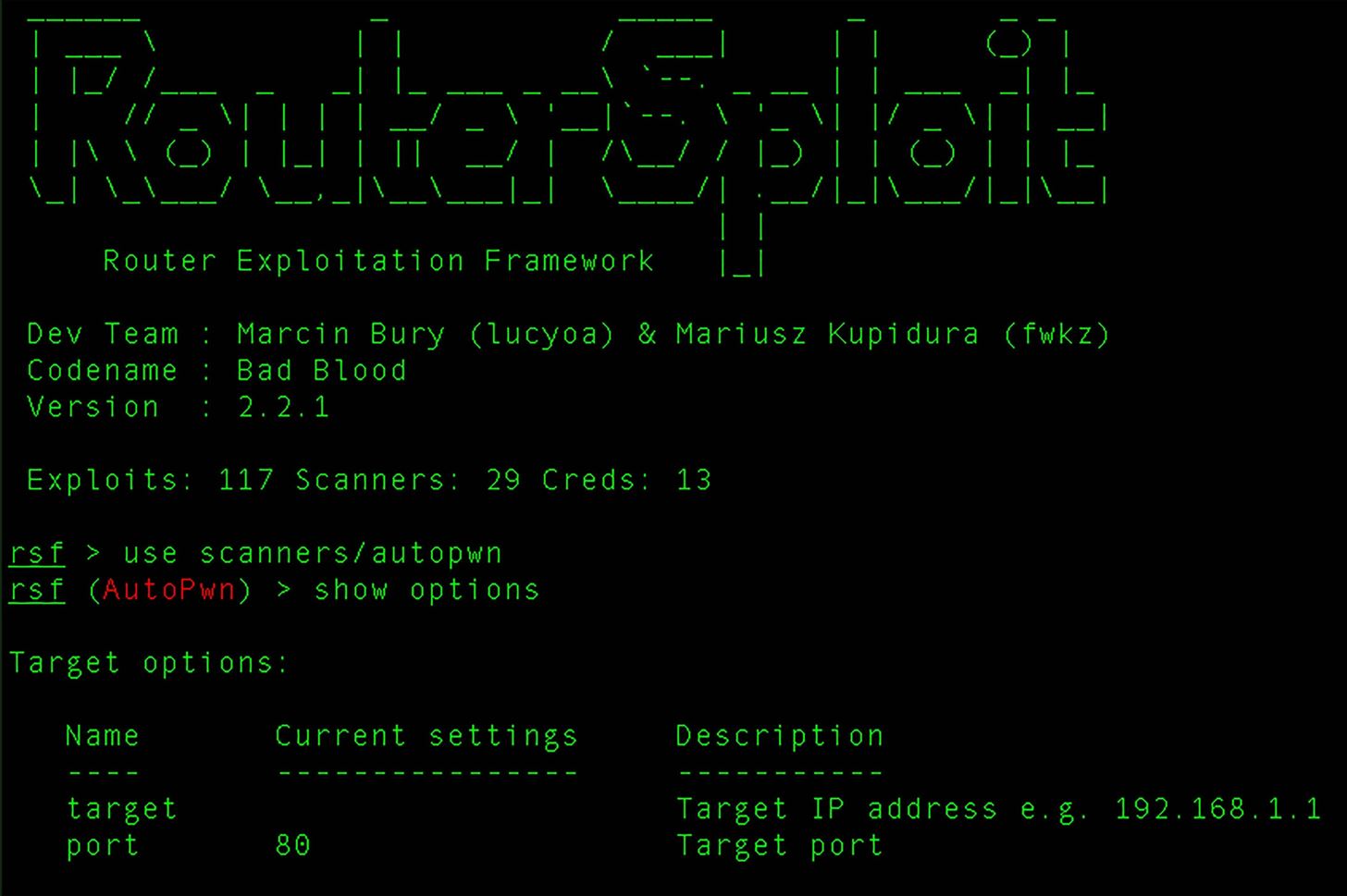


![Exploit a Router Using RouterSploit [Tutorial] - YouTube Exploit a Router Using RouterSploit [Tutorial] - YouTube](https://i.ytimg.com/vi/u0YrWfze9es/maxresdefault.jpg)