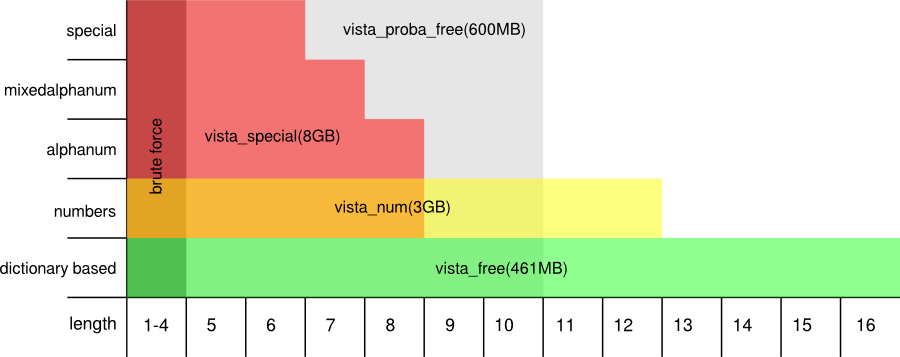
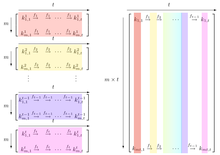
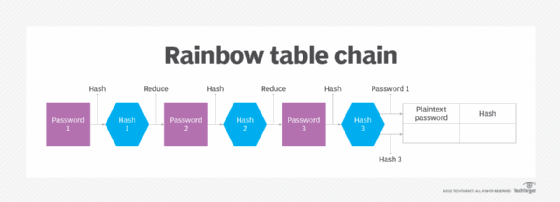
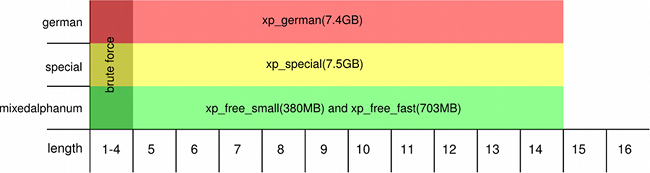
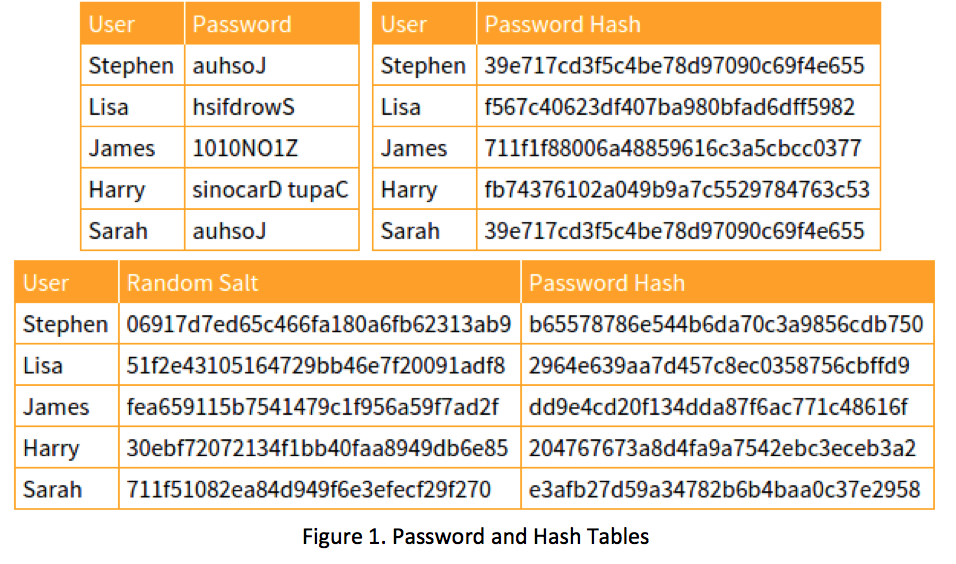
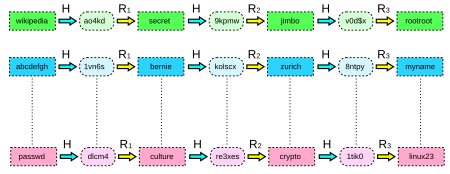
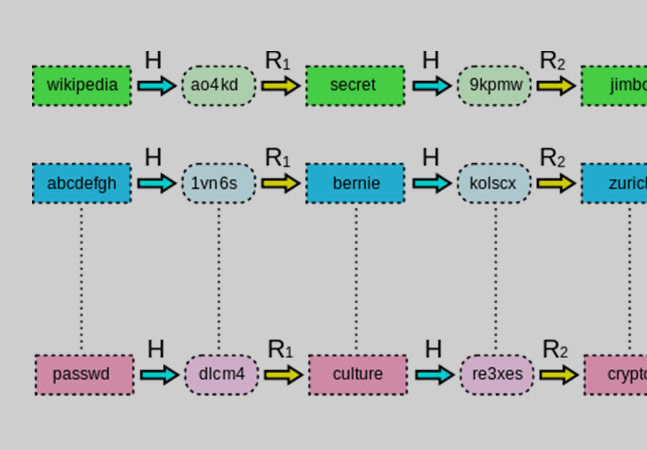
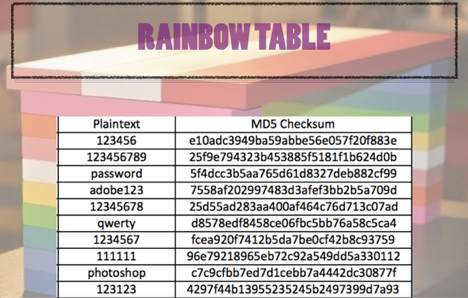
Prof B Buchanan OBE on Twitter: "Be worried about the power of the Cloud to crack hashed passwords ... the threat is not rainbow tables anymore, but Hashcat rules. You say that

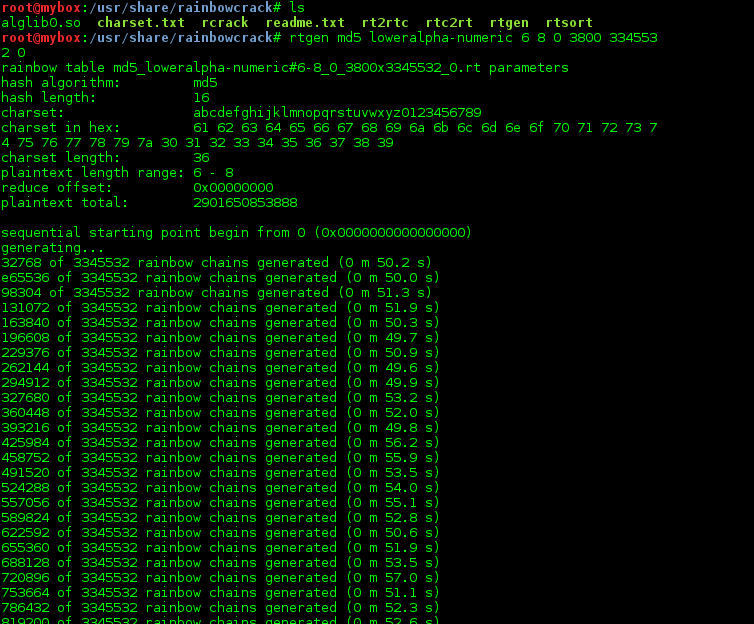
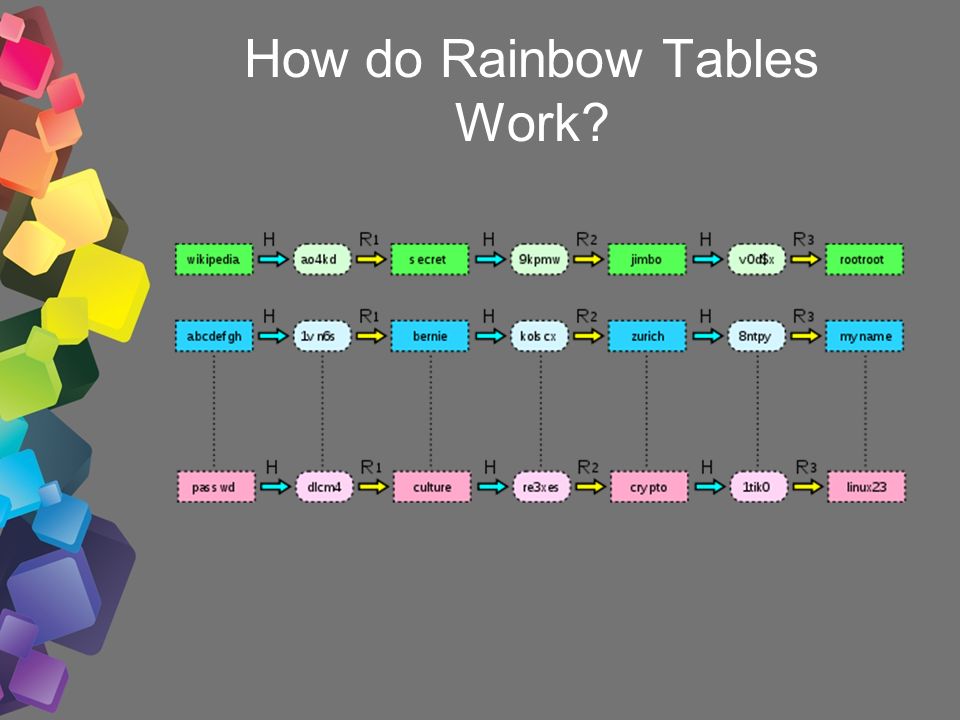
International College For Security Studies - ICSS - A rainbow table attack is a type of hacking wherein the perpetrator tries to use a rainbow hash table to crack the passwords stored

Amazon.com: 3 Pack Rainbow Tablecloths for Party Supplies, Pastel Table Covers for Cloud Birthday Decorations for Girls (54 x 108 in) : Home & Kitchen