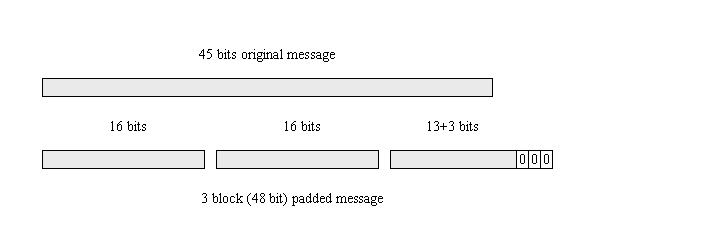
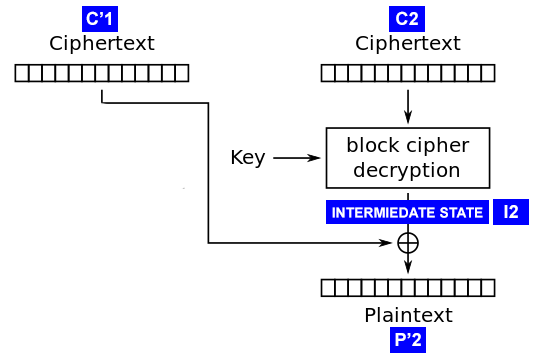
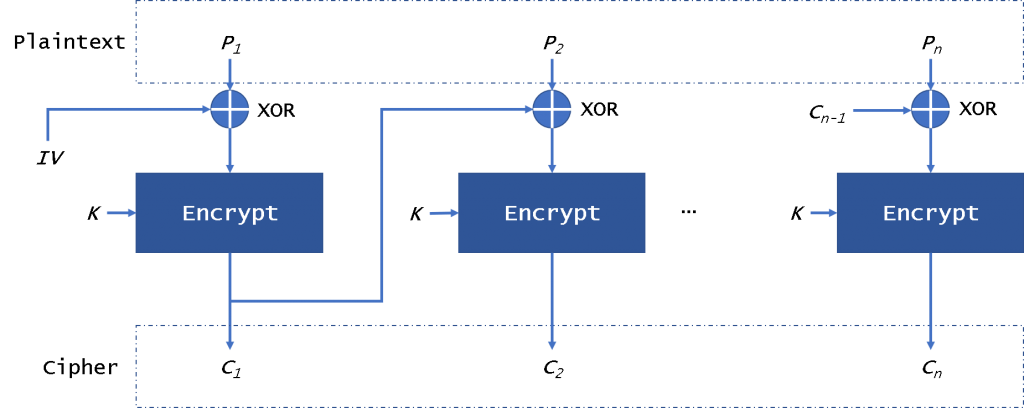
Wonk post: chosen ciphertext security in public-key encryption (Part 2) – A Few Thoughts on Cryptographic Engineering

rsa - Why PS does differ between PKCS1 v1.5 padding for signature and for encryption? - Cryptography Stack Exchange
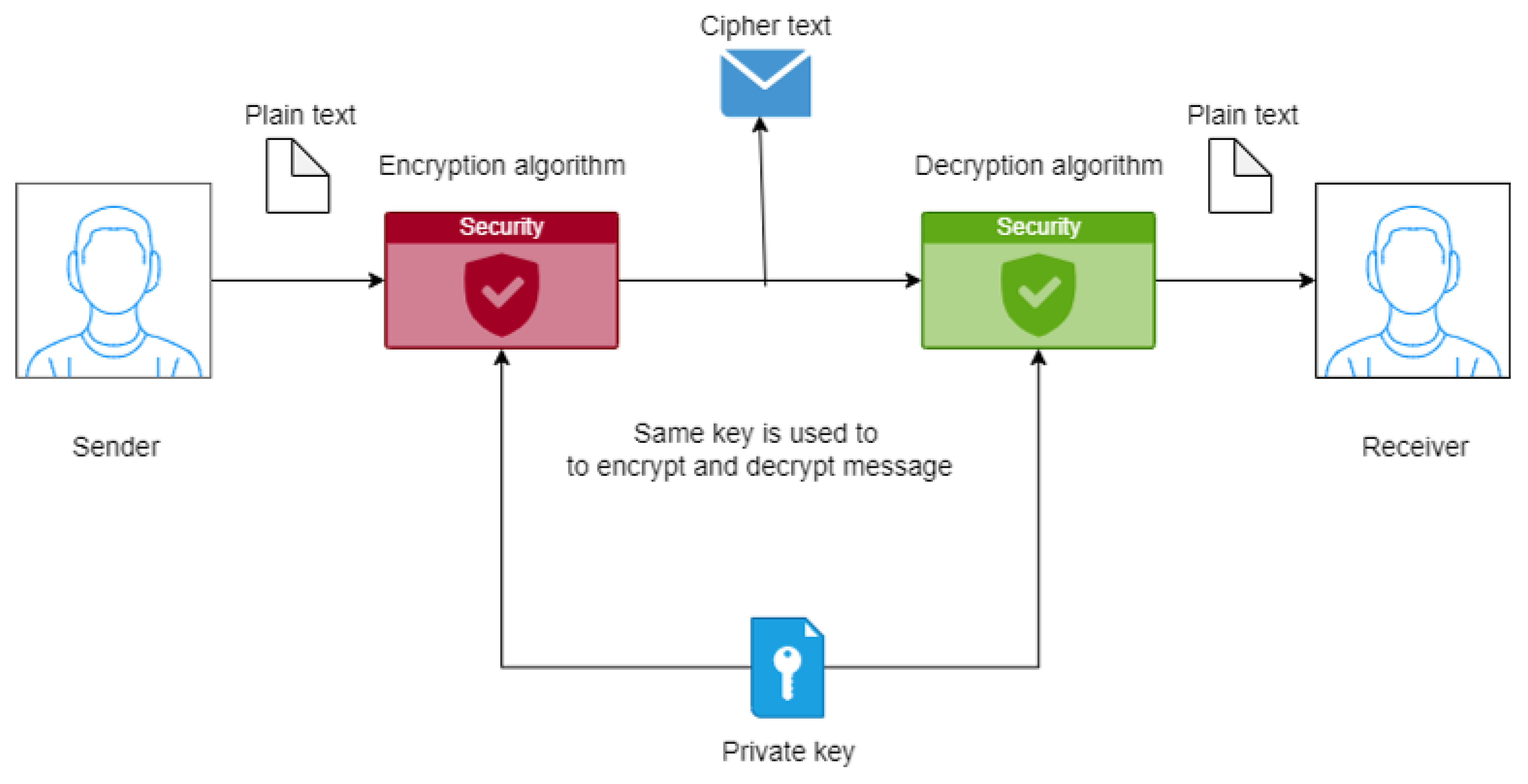
Computers | Free Full-Text | A Fast Text-to-Image Encryption-Decryption Algorithm for Secure Network Communication | HTML