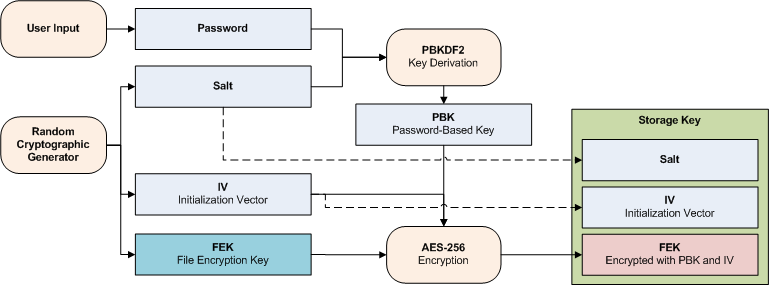
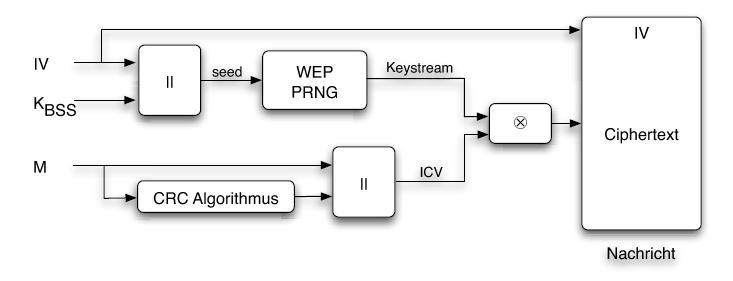
Security aspects of removing a user from an organization or collection - Vaultwarden Forum (formerly Bitwarden_RS)

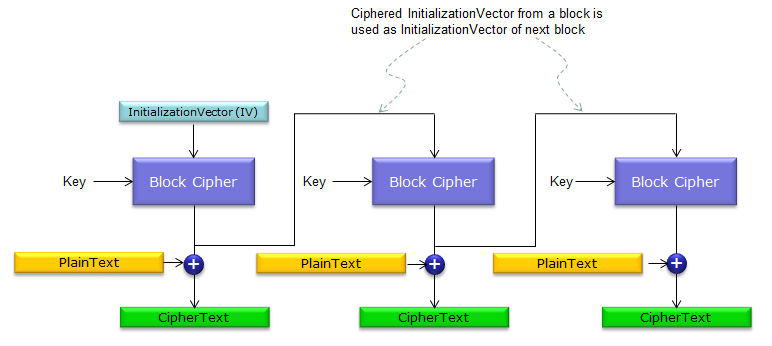
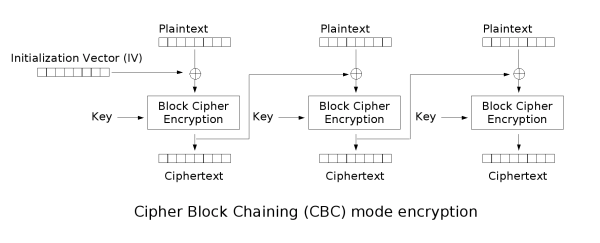
encryption - When using AES and CBC, is it necessary to keep the IV secret? - Information Security Stack Exchange
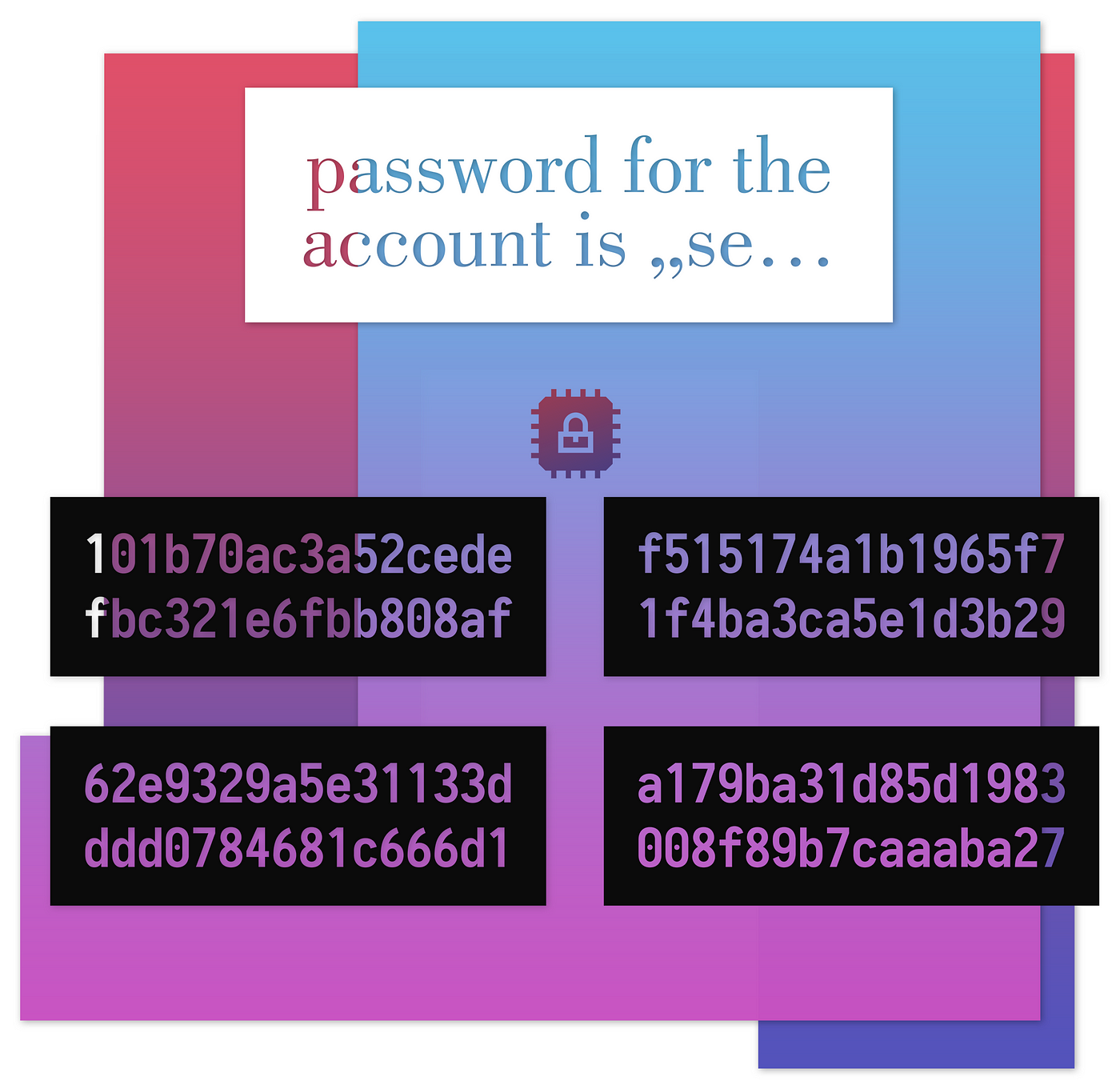
Security Best Practices: Symmetric Encryption with AES in Java and Android | by Patrick Favre-Bulle | ProAndroidDev