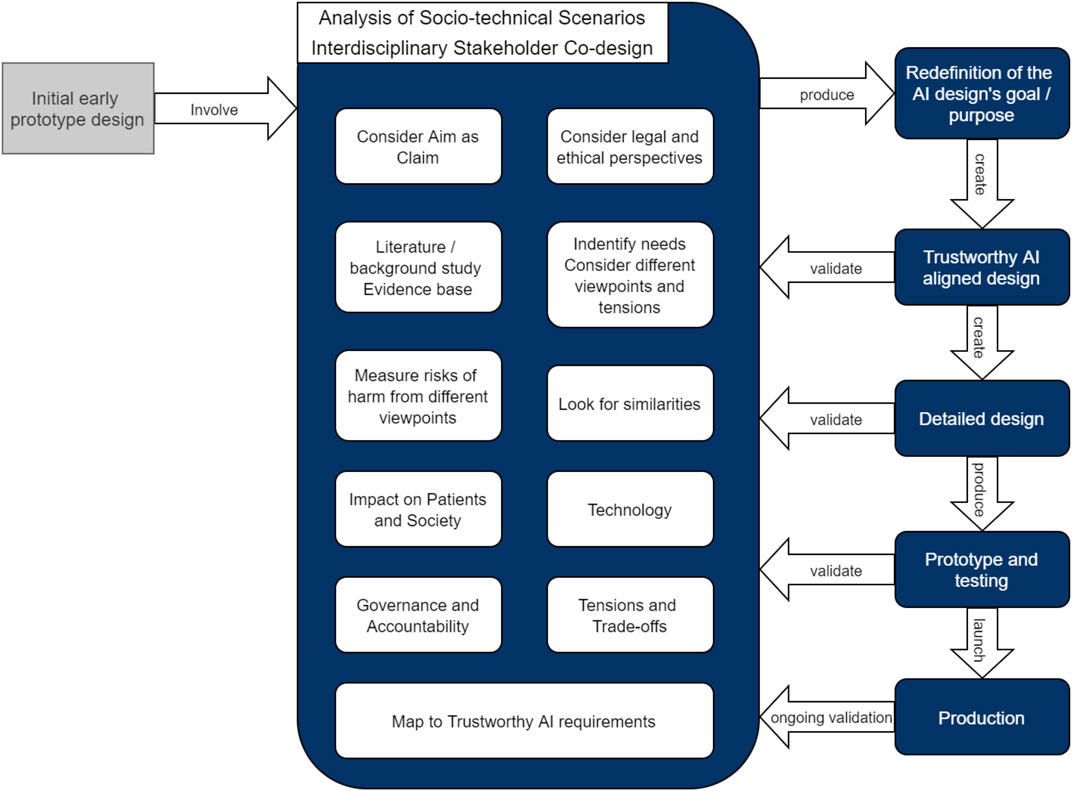
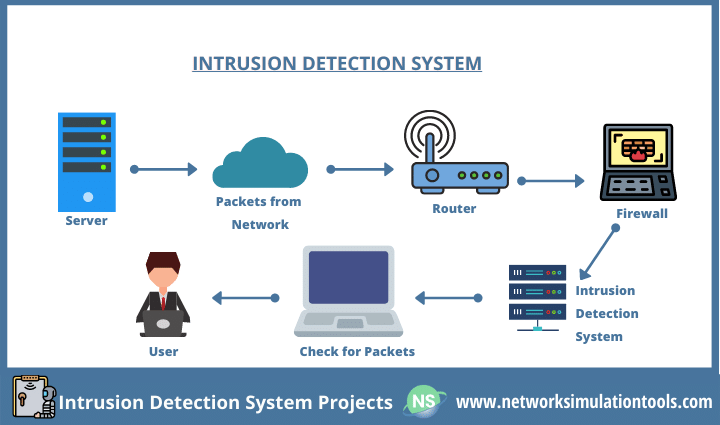
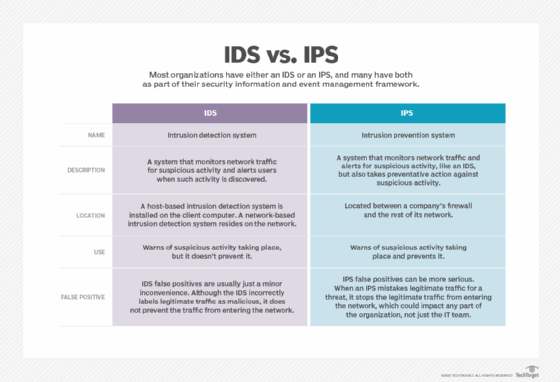
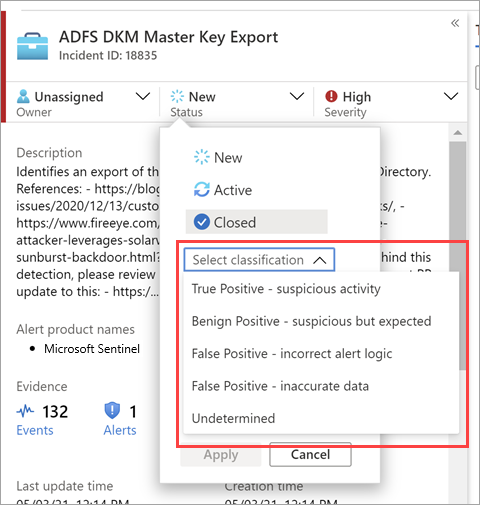
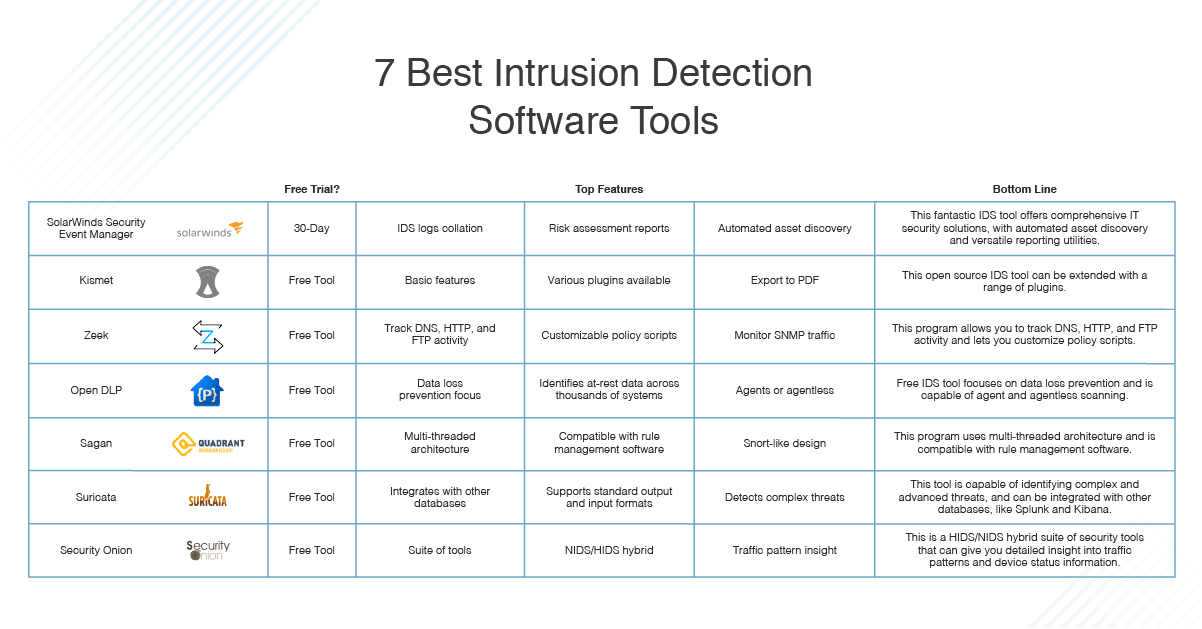
What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security

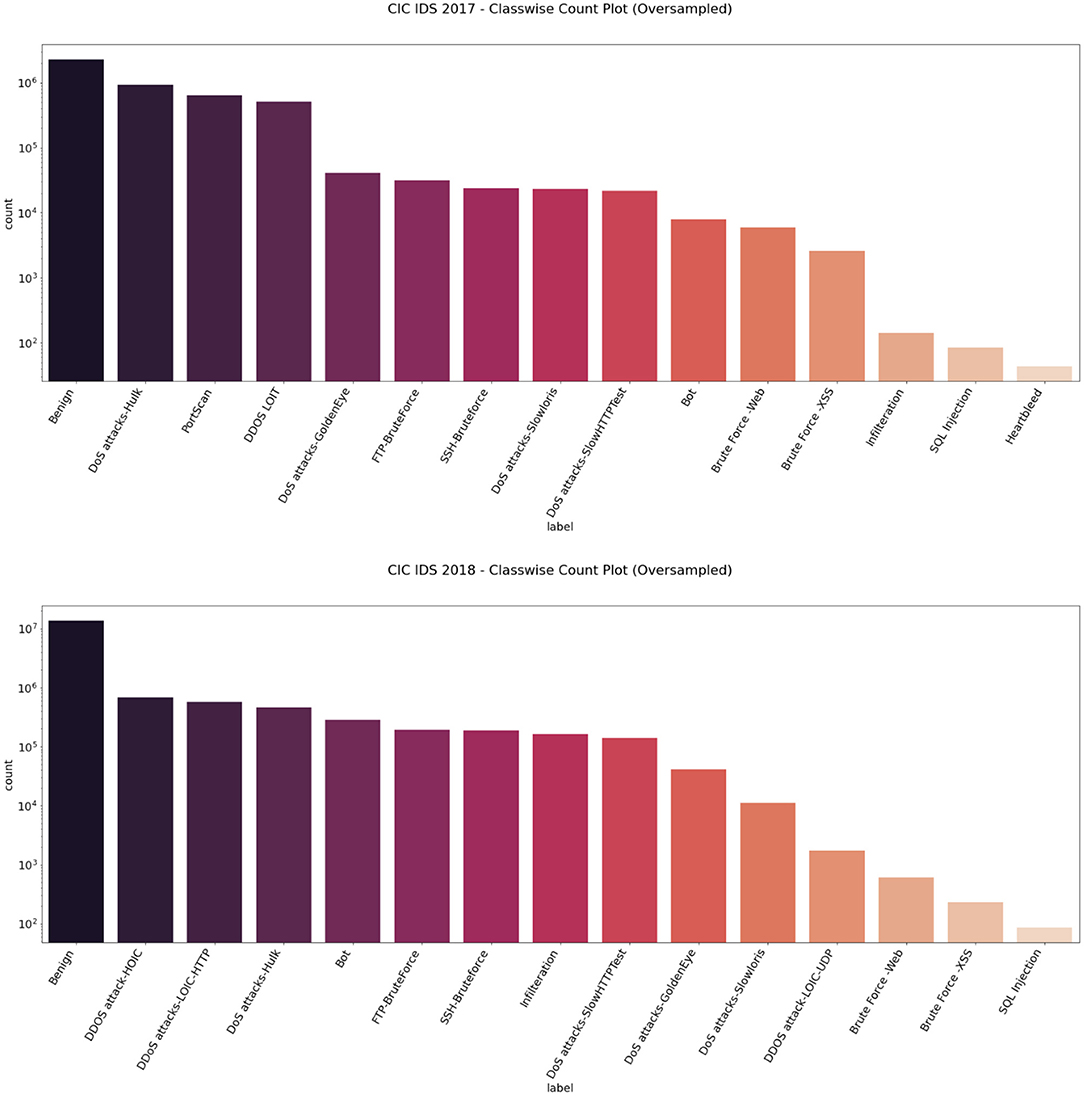
Anomaly‐based intrusion detection systems: The requirements, methods, measurements, and datasets - Hajj - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
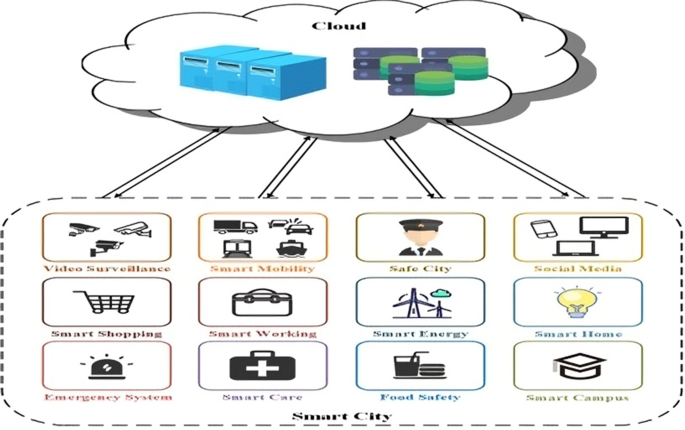
Design of Intrusion Detection System based on Cyborg intelligence for security of Cloud Network Traffic of Smart Cities | Journal of Cloud Computing | Full Text

Anomaly‐based intrusion detection systems: The requirements, methods, measurements, and datasets - Hajj - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Anomaly‐based intrusion detection systems: The requirements, methods, measurements, and datasets - Hajj - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security
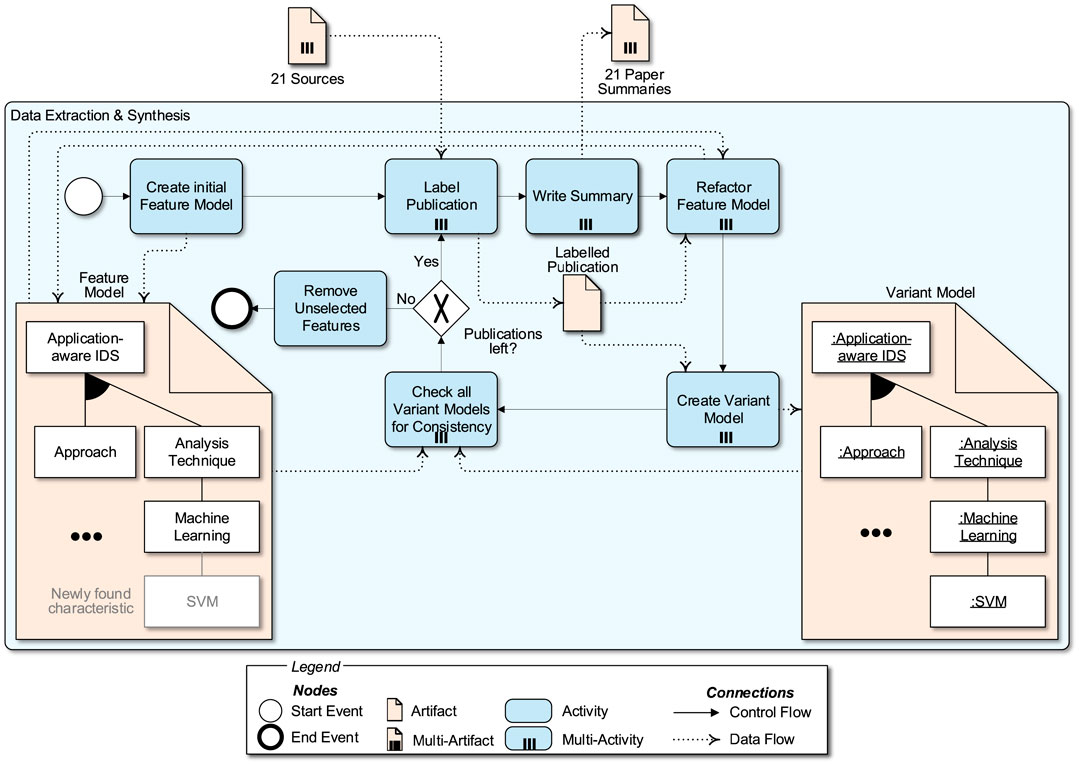
Frontiers | Application-Aware Intrusion Detection: A Systematic Literature Review, Implications for Automotive Systems, and Applicability of AutoML

What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security