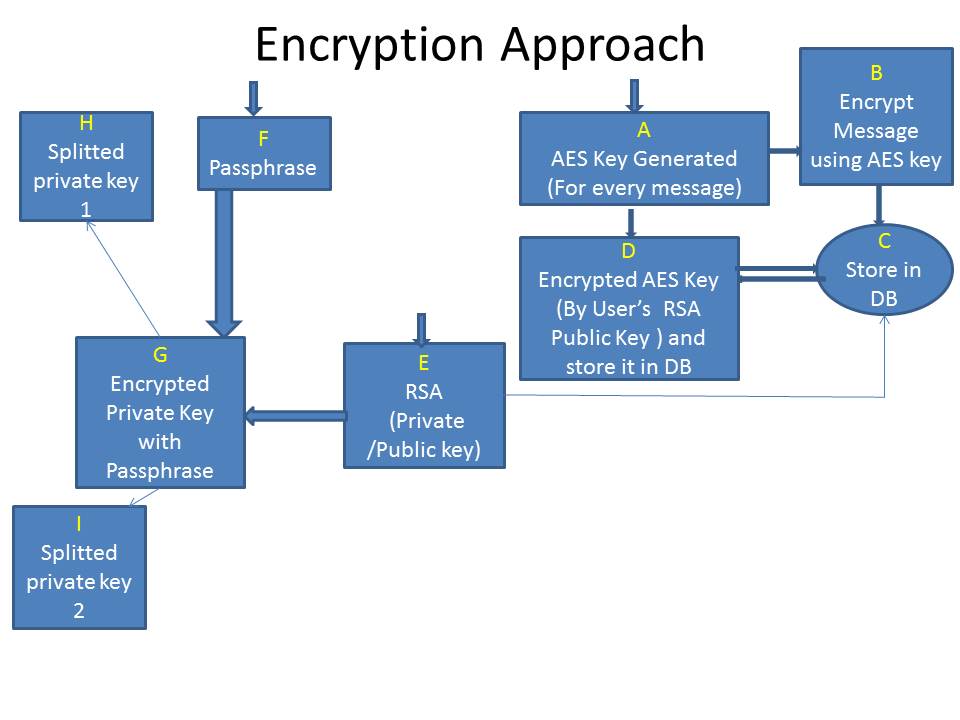
security - how to using Custom Master Key to generate plain key and encrypt key with java - Stack Overflow
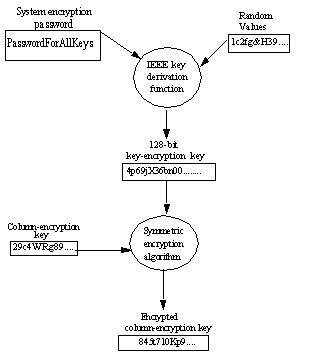
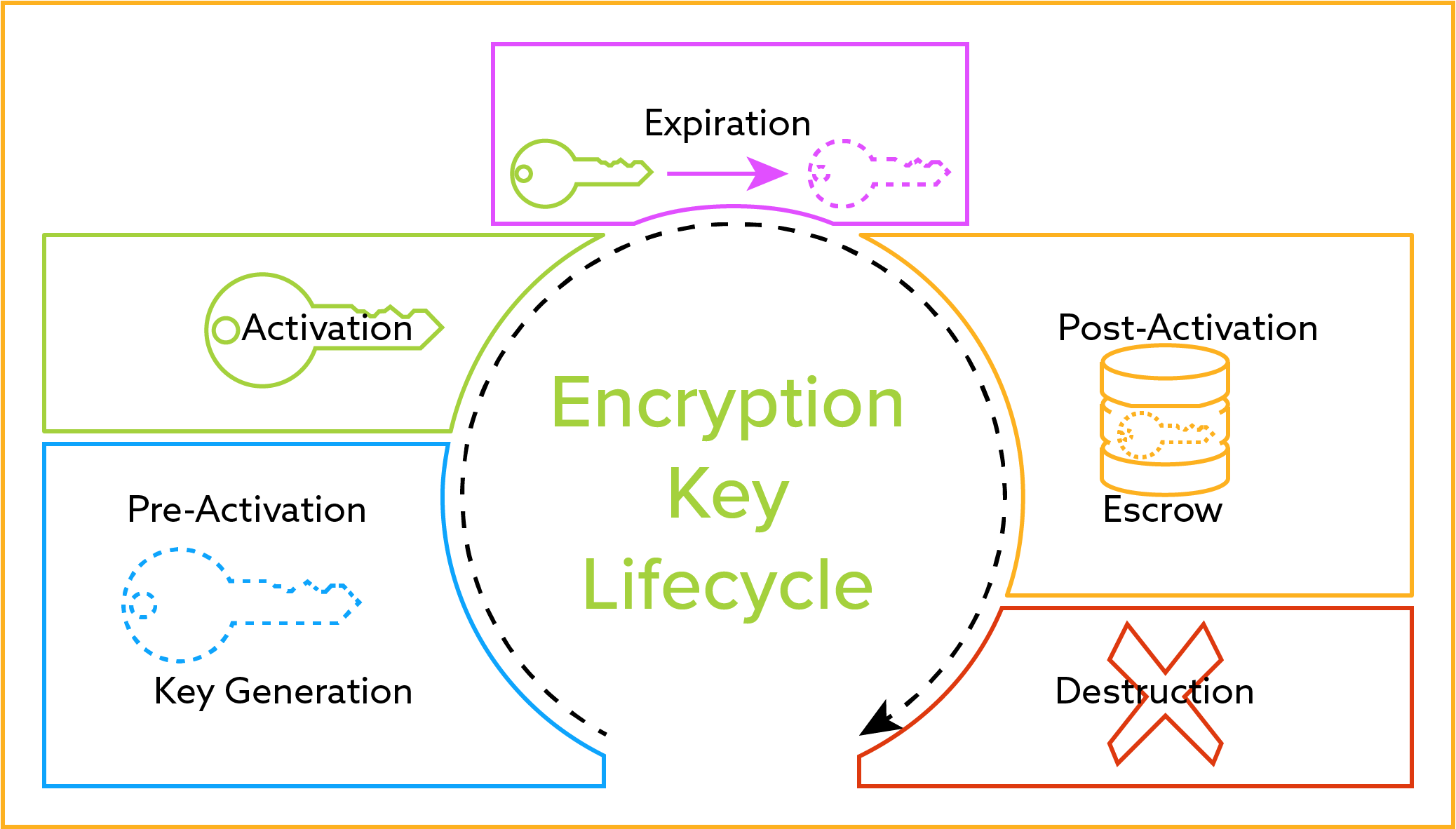
Link Key generation Encryption keys: The encryption key is generated... | Download Scientific Diagram

Link Key generation Encryption keys: The encryption key is generated... | Download Scientific Diagram