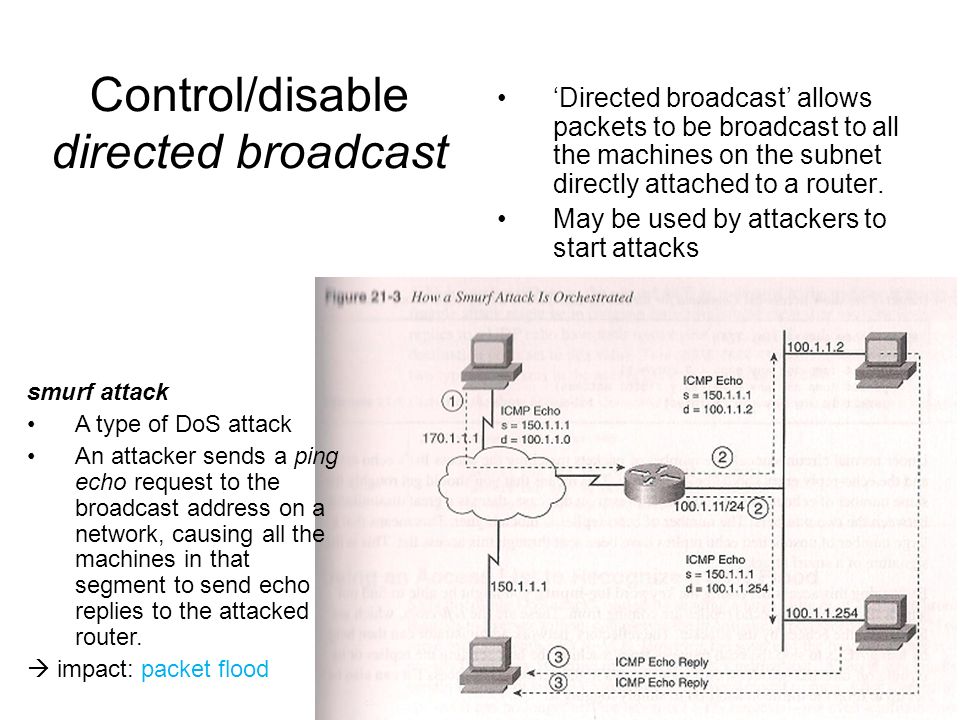
Network Security1 Secure Routing Source: Ch. 4 of Malik. Network Security Principles and Practices (CCIE Professional Development). Pearson Education. - ppt download

Wireless Access Point Protection: 5 Steps to Find Rogue Wi-Fi Networks and Comply with PCI DSS Requirement 11.1

Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press
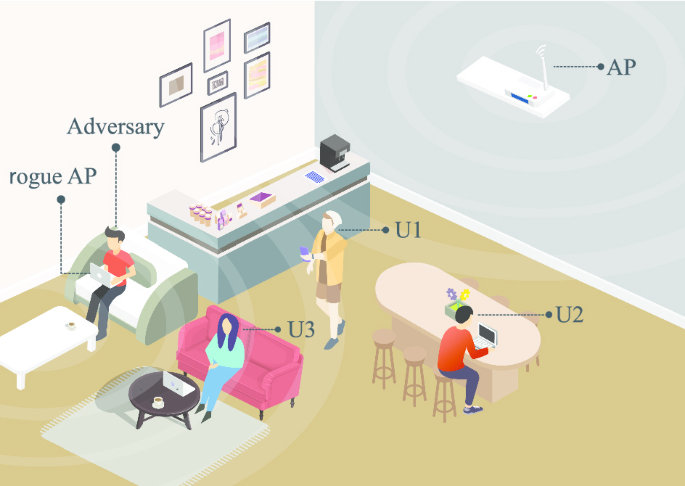
Client-side rogue access-point detection using a simple walking strategy and round-trip time analysis | EURASIP Journal on Wireless Communications and Networking | Full Text

Linksys Official Support - How to enable Rogue AP Detection on your Linksys Wireless-AC Access Point
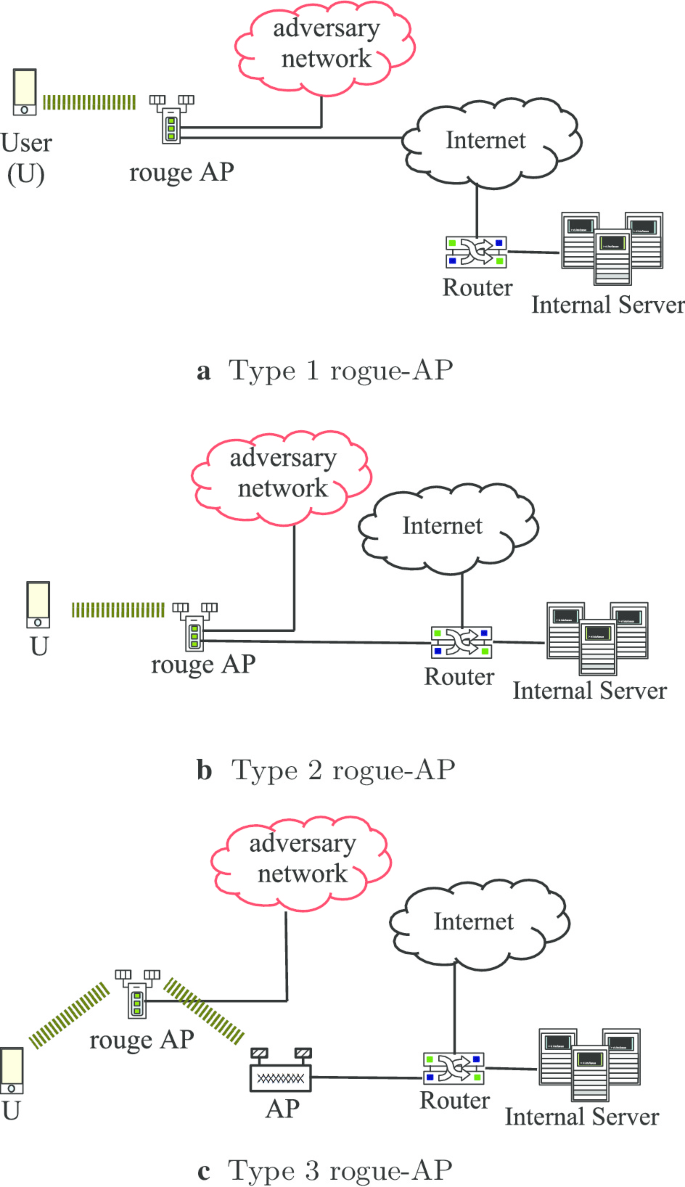


.png)

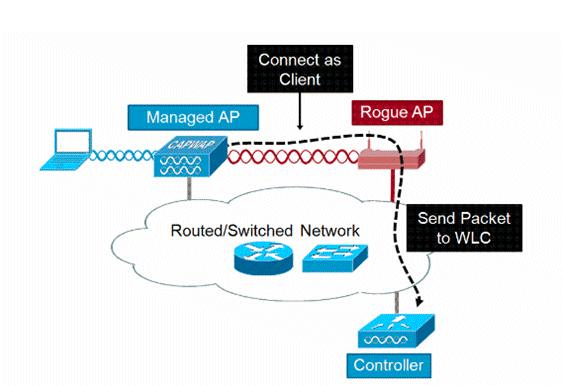


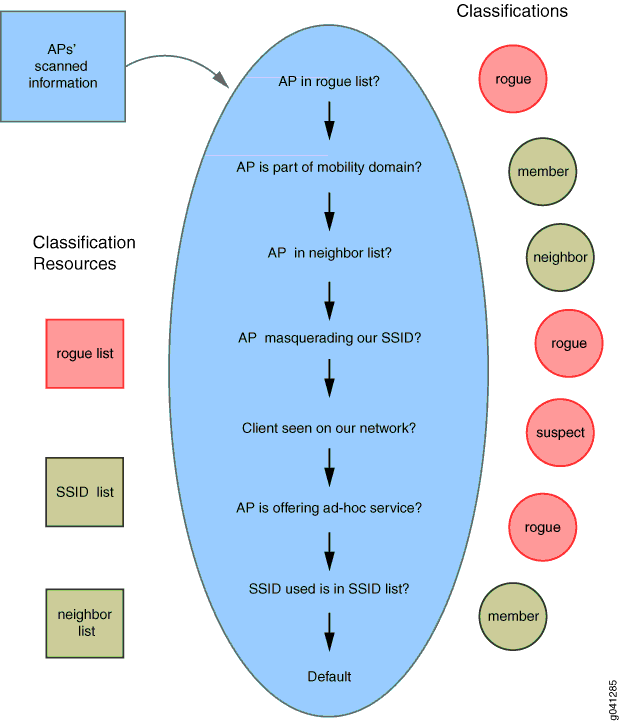

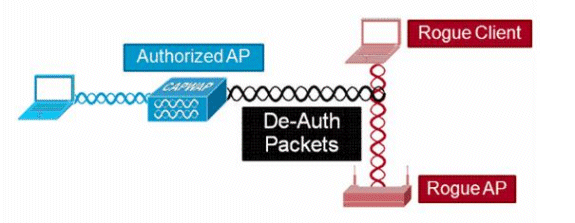

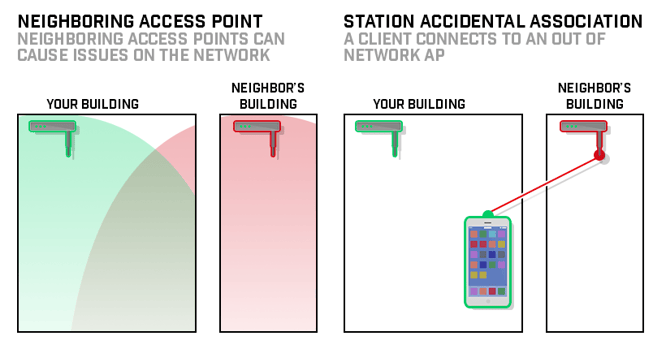
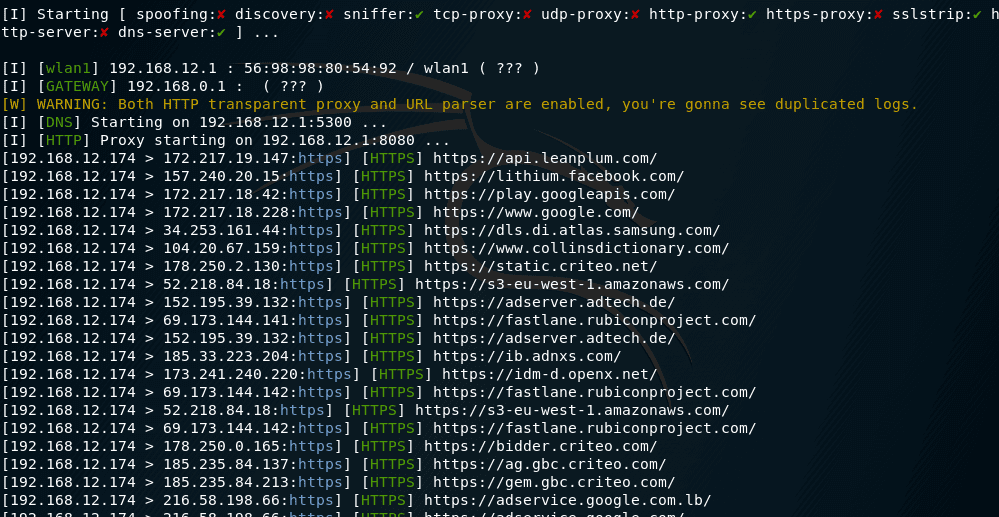

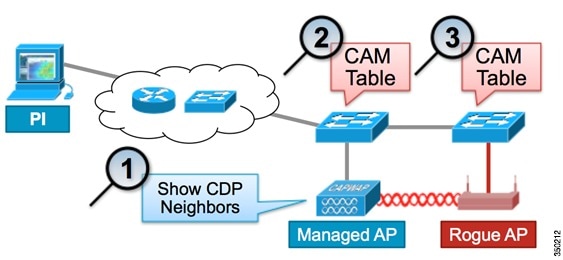
![PDF] Rogue Access Point Detection by Analyzing Network Traffic Characteristics | Semantic Scholar PDF] Rogue Access Point Detection by Analyzing Network Traffic Characteristics | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7be6ea67379a2f5bd5a4fdea66e9d3f7c9c78753/3-Figure1-1.png)
